Mini-Review: Transcend JF V60 32GB USB Flash Drive on Ubuntu
It was only just 10 years ago that some of the first USB Flash Drive storage solutions became available in the form of highly expensive sticks that only had a capacity of upwards to 32MB (yes, Megabytes) and had transfer speeds that were slower than molasses on sandpaper.
Today, we now have 32GB USB Flash Drives that go for a paltry AUD$95, and this is a review of Transcend’s offering.
I have to admit I’m a bit of sucker for Transcend. They make good products that perform well at a reasonable price, and I have bought several of their USB Flash Drive products over the last 5 years from 1GB through to 8GB. Sure, there are solutions that are much faster than Trancend, such as Corsair, but along with that comes a larger price tag. The Transcend product is competitively priced and performs more than acceptably to be used even as a boot device.
So today I obtained a 32GB stick. The package is simple – along with some catalogue advertising material, the stick itself is roughly 10mm x 50mm in size and is about 6mm deep, comes with a Transcend-branded lanyard, a removable thin clear plastic layer on the burgundy-coloured part of the stick to protect it from scratches and that’s pretty much it. The non-retractable USB connector is protected by a removable plastic cap. Refreshingly, the cardboard insert from the packaging actually makes reference to Linux as a supported platform, citing a requirement of kernel 2.4.2 or later.

Like all sticks these days, this USB 2.0 unit is pre-formatted to FAT32 thus allowing it to work with pretty much every major platform out there. Personally I rarely use my sticks on Windows PC’s, though I keep an 8GB stick handy with FAT32 just in case. Most of the time, however, I reformat them to EXT2 or EXT3.
So, let’s plug this guy in. It’s always interesting to see how they implement the activity LED (well OK, it’s hardly anything to write home about, but I’ve got to generate some excitement somehow…!). Previous Transcend sticks had an obvious dot on the top, usually sporting a blue LED as has been the trend for the last few years, but this time they’ve gone different. There is no obvious hole on the stick for an activity light and upon connecting it to my PC’s front USB ports, the end of the stick suddenly lit up in bright roadwork-vest-orange. Well, that’s a welcome change. I can leave it plugged in a dark room without it becoming distracting! The LED remains on all the time to show that it is active and flashes HDD-style when there is activity.

Nautilus popped up its usual “what do you want to do” prompt and I elected to open a window. As typical with most USB Flash Drives, this one came up imaginatively titled “disk” which is Ubuntu’s way of telling you that the stick has no actual label. The stick itself is completely empty – no promotional software or funky one-touch-backup applications are included.
First thing was first – relabel that stick. There’s nothing worse than having several USB Flash Drives and not knowing what’s on them at a glance. I fired up Ubuntu’s Partition Editor (GParted) and had a look at the stick. The stick’s actual storage space is 29.92GB and I observed that the leading 4MB were not allocated. Usually you find most Windows-formatted devices have the last few MB unallocatable, not that it actually matters.

Anyway, I quickly unmounted the stick and renamed it and remounted it. For those that are interested, this is what the dmesg output for it looks like:
usb 8-3: new high speed USB device using ehci_hcd and address 8 usb 8-3: configuration #1 chosen from 1 choice scsi19 : SCSI emulation for USB Mass Storage devices usb-storage: device found at 8 usb-storage: waiting for device to settle before scanning usb-storage: device scan complete scsi 19:0:0:0: Direct-Access JetFlash Transcend 32GB 8.07 PQ: 0 ANSI: 2 sd 19:0:0:0: [sdf] 62750720 512-byte hardware sectors (32128 MB) sd 19:0:0:0: [sdf] Write Protect is off sd 19:0:0:0: [sdf] Mode Sense: 03 00 00 00 sd 19:0:0:0: [sdf] Assuming drive cache: write through sd 19:0:0:0: [sdf] 62750720 512-byte hardware sectors (32128 MB) sd 19:0:0:0: [sdf] Write Protect is off sd 19:0:0:0: [sdf] Mode Sense: 03 00 00 00 sd 19:0:0:0: [sdf] Assuming drive cache: write through sdf: sdf1 sd 19:0:0:0: [sdf] Attached SCSI removable disk sd 19:0:0:0: Attached scsi generic sg6 type 0
Exciting stuff. ![]()
With my now-properly-named stick, it was time to do some read/write tests. The stick comes preformatted as FAT32, so we’ll use that, but at the same time I will also conduct some tests using Linux-native filesystems. In this case, EXT3. Our test data will be a series of 15,645 thumbnail images, each averaging about 18K in size. We will also do a large file copy test using a compressed high-definition video file at 3.1GB in size. We will time how long it takes to copy this data to the USB Flash Drive and calculate the transfer speed from that. Then we will reboot the machine, to ensure no data is cached, and copy that data back from the USB stick to measure the read speed.
For comparison, we will also do the EXT3 tests with an older (6 month old) 8GB USB Flash Drive, also made by Transcend, to see if there has been a notable change in read or write speed between products.
First up, the small file copy test. Our test data is 15,645 thumbnail files from our host PC’s hard-drive, each averaging about 18K in size (total 281MB).
- Using the FAT32 filesystem on the 32GB stick, copying the small files took 12 minutes to copy at approximately 345K per second. Ouch – slow.
- Using the Ext3 filesystem on the 32GB stick, copying the same files took only 2 minutes and 53 seconds at a rate of approximately 1.6MB per second. Much better.
- And using the EXT3 filesystem on the older 8GB stick, copying the same data took only 2 minutes and 40 seconds, just edging out the 32GB stick.


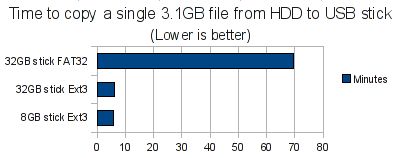
Now for the large file copy test. Our test data is a single 3.1GB high-definition video file being copied from the host PC’s hard-drive.
- Using the FAT32 filesystem on the 32GB stick, copying the large file took a pathetic 69 minutes and 24 seconds to transfer, or about 780K per second. It really shows that FAT32 really does not like large files at all.
- Using the Ext3 filesystem on the 32GB stick, copying the same file took a far more respectable 6 minutes and 16 seconds to complete at approximately 8.4MB per second.
- Finally, the Ext3-formatted 8GB stick copied the file in 5 minutes and 55 seconds, which beats the 32GB stick, but only by about 20 seconds and half a megabyte per second (8.9MB/s).

To be fair, Windows’ NTFS filesystem should show reasonably similar figures to Ext3, but I did not test that as this article is about Ubuntu, not Windows! ![]()
Finally, we have the read-test. We rebooted the host PC to clear any cached data and copied only the 3.1GB large file from the USB stick to the host PC’s hard-drive.
- The FAT32-formatted 32GB stick copied the file in 3 minutes and 13 seconds. Exponentially faster than its write action.
- The EXT3-formatted 32GB stick took 2 minutes and 32 seconds to copy the file.
- The EXT3-formatted 8GB stick by comparison did the same copy in 3 minutes and four seconds. Interesting that it’s a slow reader compared to the 32Gb stick, but a slightly faster writer.


So transfer speeds have largely remained unchanged between generations, which is a Good Thing(TM) – if there is any faster speed, then that’s a bonus, but the last thing you want is greater capacity at a tragic expense of transfer speed, and whilst we do have that discrepancy here, it’s negligible at best.
Conclusion
Trancend’s 32GB USB Flash Drive is not the largest currently-available on the market, but it is certainly one of the most affordable and has good performance to boot. Aesthetically, the white plastic looks and feels a little cheap, but the stick as a whole feels robust and could probably take a few knocks without having a fit. The lanyard included is more than adequate to hang around your neck with, and the overall size of the stick means you could also comfortably add it to your keyring or hip pocket without it getting in the way, though the separate USB cap could probably be easily lost in that instance.
Review score: 8 out of 10






 .
.



 With a little help from a few external resources including the
With a little help from a few external resources including the 









